Maximizing Configuration Quality in Kubernetes with Kubeconform
Written on
Chapter 1: Understanding the Evolution of Kubernetes
Kubernetes is constantly evolving, with frequent updates that introduce new features while phasing out older ones. As discussed in prior articles—such as those focusing on Autoscaling v2 and Vertical Autoscaling—it's crucial to stay updated on these changes.
When the API version of certain objects shifts, such as transitioning from v1/alpha to v1/beta or moving to a stable v1, it can create compatibility issues. Therefore, ensuring that your manifests align with the version you are deploying is essential. Tools like Kubeconform can assist in this regard.
Section 1.1: What is Kubeconform?
Kubeconform is a robust tool specifically designed for managing and validating Kubernetes configurations. With Kubernetes becoming the preferred platform for container orchestration, maintaining the integrity and accuracy of configuration files is vital. Kubeconform meets this demand by offering a comprehensive suite of validation tools that check configuration files against established standards or custom rules.
This utility supports various Kubernetes versions, enabling you to validate configurations against different API versions. This feature is particularly useful when dealing with clusters that operate on different versions of Kubernetes or when transitioning applications across environments with varying setups.
Subsection 1.1.1: Enforcing Best Practices
One of Kubeconform's standout features is its ability to enforce best practices and standards within Kubernetes configurations. Users can define rules—such as requiring proper labels, setting resource limits, or implementing security policies—and Kubeconform will validate configuration files against these criteria. This proactive approach helps identify potential issues early and ensures compliance with established guidelines.
How to Install Kubeconform?
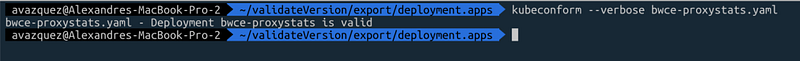
How to Run Kubeconform from the Command Line?
Kubeconform is delivered as a lightweight binary intended for command-line execution. It maintains a minimal interface to ensure compatibility, requiring users to specify the file or directory containing the manifest files for validation, as demonstrated below:
Additionally, Kubeconform offers several options for further customization, including:
- -ignore-filename-pattern: Specify paths to ignore using regular expressions (can be applied multiple times).
- -ignore-missing-schemas: Bypass files lacking schemas instead of failing the validation.
- -Kubernetes-version: Indicate the Kubernetes version for validation, e.g., 1.18.0 (default is "master").
- -output: Choose the output format—json, junit, pretty, tap, text (default is "text").
- -reject: List of kinds or GVKs to reject, separated by commas.
- -skip: List of kinds or GVKs to ignore, separated by commas.
- -strict: Prohibit additional properties not included in the schema or duplicate keys.
- -summary: Display a summary at the end (ignored for junit output).
Section 1.2: Use Cases for Kubeconform
Kubeconform is beneficial in various scenarios. One significant use case involves Kubernetes upgrades; it ensures that your current manifest remains compatible with the new release your cluster will adopt. This validation process helps confirm that your YAML configurations will work seamlessly with the latest version.
Moreover, Kubeconform integrates effortlessly into existing CI/CD pipelines. By incorporating it as a validation step prior to deployment, teams can catch configuration errors early in the development cycle, thereby reducing the chances of deployment failures and enhancing configuration consistency.
In addition to validation, Kubeconform offers valuable feedback and suggestions for enhancing Kubernetes configuration files. It identifies specific issues or deviations from defined rules and provides guidance for resolution, simplifying troubleshooting and aiding developers and administrators in adhering to best practices.
Conclusion
Kubeconform is an essential tool for Kubernetes practitioners aiming for reliable and consistent deployments. It empowers teams to uphold high standards of configuration quality, minimizes the risk of misconfigurations, and bolsters the overall stability and security of applications built on Kubernetes.