How to Achieve Online Anonymity with Linux Tools
Written on
Chapter 1: Understanding Digital Privacy
In our current digital world, the monitoring of online activities has become commonplace. Major corporations such as Google and Microsoft track every search query, keystroke, and click to market to advertisers, hoping to influence your purchasing decisions. While advertisements are essential for maintaining a free internet, the constant surveillance by tech giants can be unsettling. Moreover, it’s not just advertisers who exploit personal data; cybercriminals and malicious entities are always on the lookout for opportunities to misuse your digital footprint for profit. In this guide, I will introduce two effective tools that can help you regain control over your online privacy using Linux.

Chapter 2: Exploring Tails OS
The first video titled "How to be Invisible Online (and the hard truth about it)" delves into the complexities of maintaining privacy in the digital age, discussing various strategies and tools, including Tails OS.
Tails is a Linux distribution based on Debian, highly praised for its robust privacy features. It boasts a user-friendly interface, making it accessible to everyone, and comes with a suite of security tools preinstalled to ensure complete anonymity online. However, it's important to note that Tails is exclusively designed for privacy-focused tasks and is not recommended for gaming, media production, or casual browsing. To maximize its potential, you should install Tails on a bootable USB drive, allowing you to connect it to any public or personal computer and instantly become anonymous wherever you go.
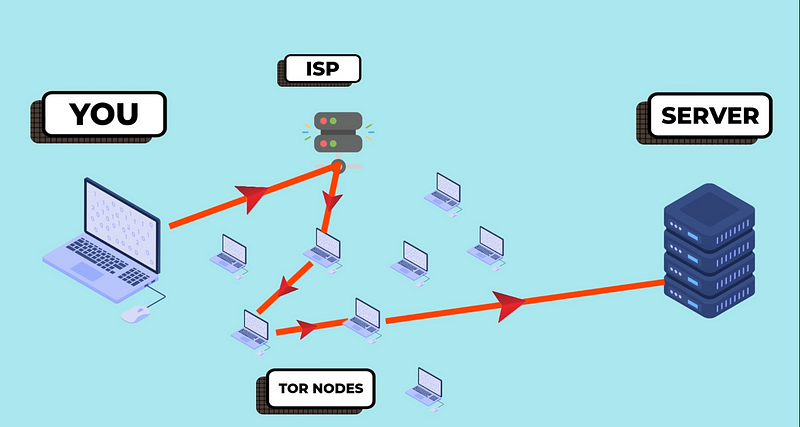
The primary defense offered by Tails is its integration with the TOR network. TOR conceals your IP address by routing your data through multiple TOR nodes before reaching its final destination. As a result, if the destination server attempts to trace your IP, it will only see the last node in the chain, which is an unrelated IP address. Furthermore, all data transmitted via TOR is encrypted, rendering it unreadable to anyone attempting to intercept your communications.
Chapter 3: The Role of Amnesia
Amnesia is a built-in application within the Tails environment that automatically deletes the usage history of any application you access. Since Tails operates from a USB drive, Amnesia serves as an excellent companion for achieving total privacy. You can plug in the USB, browse the internet freely, and once you remove the USB, no trace is left behind for subsequent users of that computer. Amnesia does allow you to select specific programs to retain on the system, but it is recommended to avoid this for maximum privacy.
While these tools significantly enhance your anonymity, it is important to acknowledge that complete invisibility online is unattainable. For instance, if you log into a website using your personal credentials, that site will inherently recognize who you are and the data associated with your account. Although they may not track your location or monitor your entire online presence, your identity is still exposed. Nevertheless, utilizing these privacy tools can significantly empower you to regain your independence and achieve a higher degree of invisibility on the internet.
Chapter 4: Further Insights on Online Privacy
The second video titled "Become Invisible Online With Tails OS, Incognito Linux System Recommended by Edward Snowden" provides a comprehensive overview of Tails OS, highlighting its features and practical applications for maintaining privacy online.
If you enjoyed this article, please consider supporting my work by subscribing to access unlimited Medium articles for just $5 per month or $50 per year. Thank you for your support!